CrowdStrike users BEWARE! India's cyber security agency issues warning after recent Microsoft outage
Synopsis
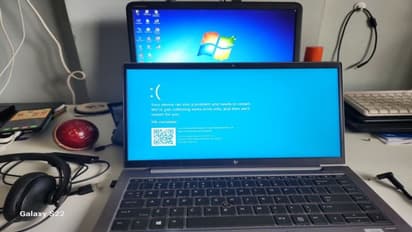
The Indian Computer Emergency Response Team (CERT-In) has issued an advisory warning against phishing attack campaigns targeting users impacted by the recent Microsoft Windows outage. Microsoft Windows suffered a worldwide outage due to a faulty update to the CrowdStrike Falcon Sensor software.
The Indian Computer Emergency Response Team (CERT-In) has issued an advisory warning against phishing attack campaigns targeting users impacted by the recent Microsoft Windows outage. The Ministry of Electronics and Information Technology oversees the national cyber security organisation, CERT-In. An error in the CrowdStrike Falcon Sensor software upgrade caused a global outage for Microsoft Windows. As a result, the Microsoft Windows operating system crashed, affecting systems in hospitals, banks, and aeroplanes all around the world.
According to CERT-In's advice, there have been allegations of a persistent phishing effort that targets users of CrowdStrike and uses the worldwide tech outage problem as cover for its nefarious operations. These include, among other things, calling consumers and pretending to be from CrowdStrike assistance, sending phishing emails, and offering software scripts that promise to automatically fix the content update problem.
The advisory further states that scammers are using this issue to distribute trojan malware pretending to be recovery tools. These attack campaigns, it says, could entice an unsuspected user to install unidentified malware, which could lead to sensitive data leakage, system crashes and data loss.
The warning goes on to say that con artists are taking advantage of this vulnerability to spread trojan software under the guise of recovery tools. It claims that these assault tactics may persuade an unwary user to download and install unknown malware, which may result in the loss of data, system failures, and the disclosure of private information.
Additionally, the CERT-In provides a list of URLs that businesses should think about blocking connections to when setting up their firewall rules. These include: Further, the CERT-In lists URLs that organizations may consider configuring their firewall rules to block connections to. These include:
- crowdstrike.phpartnersHorg
- crowdstrike0dayMcom
- crowdstrikebluescreen[.]corn
- crowdstrike-bsod[.]com
- crowdstrikeupdate[.]com
- crowdstrikebsod[.]corn
- www.crowdstrike0day[.]com
- www.fix-crowdstrike-bsod[.]com
- crowdstrikeoutage[.]info
- www.microsoftcrowdstrike[.]corn
- crowdstrikeodayINcom
- crowdstrike[.]buzz
- www.crowdstriketoken[.]com
- www.crowdstrikefix[.]com
- fix-crowdstrike-apocalypse[.]com
- microsoftcrowdstrike[.]com
- crowdstrikedoomsday[.]com
- crowdstrikedown[.]com
- whatiscrowdstrike[.]corn
- crowdstrike-helpdesk[.]corn
- crowdstrikefixMcorn
- fix-crowdstrike-bsodHcorn
- crowdstrikedown[.]site
- crowdstuck[.]org
- crowdfalcon-immed-update[.]com
- crowdstriketoken[.]com
- crowdstrikeclaim[.]com
- crowdstrikeblueteam[.]corn
- crowdstrike-office365Hcom
- crowdstrikefix[.]zip
- crowdstrikereport[.]com
Find the latest Technology News covering Smartphone Updates, AI (Artificial Intelligence) breakthroughs, and innovations in space exploration. Stay updated on gadgets, apps, and digital trends with expert reviews, product comparisons, and tech insights. Download the Asianet News Official App from the Android Play Store and iPhone App Store for everything shaping the future of technology.